In his recent piece, “America Hits the Global Snooze Button” in The Wall Street Journal, Walter Russell Mead, the James Clarke Chace Professor of Foreign Affairs and Humanities at Bard College and a scholar at the Hudson Institute underscores the critical nature of current global threats, echoing a sentiment that I wholeheartedly share. The urgency cannot be overstated: China’s aggressive expansion, Russia’s advances in Ukraine, and Iran’s destabilizing actions in the Middle East constitute a significant and multifaceted threat to global stability. This demands stronger U.S. armed forces to counter these threats effectively.
The situation around Taiwan, the South China Sea and the Philippines exemplifies the complexities we face. China’s assertive territorial claims and militarization of the region threaten not only our allies but also global trade routes. It necessitates a stronger U.S. naval presence and support for regional partners. The Middle East is increasingly volatile and involves contested waters of the eastern Mediterranean, the Red Sea and the Persian Gulf. The U.S. Navy is the only effective naval force to counter the threats there and it is stretched thin.
Moreover, it is alarming to consider that our defense systems have potentially been compromised, which could be construed as an act of war. Yet, many Americans remain oblivious to these dangers, and who can blame them? After decades of conflict with little to show for it, the American public feels disillusioned, cheated, and exhausted. They see corruption and self-interest within the military-industrial complex and feel that politicians are complicit in perpetuating these issues.
The prevailing sentiment of mistrust extends to the government itself. Some argue for a more isolationist approach, focusing solely on defending our shores, while others, particularly younger generations, feel disenfranchised and disconnected from these geopolitical issues. This disconnect is further exacerbated by a widespread lack of historical knowledge, a consequence of its declining emphasis in our education system.
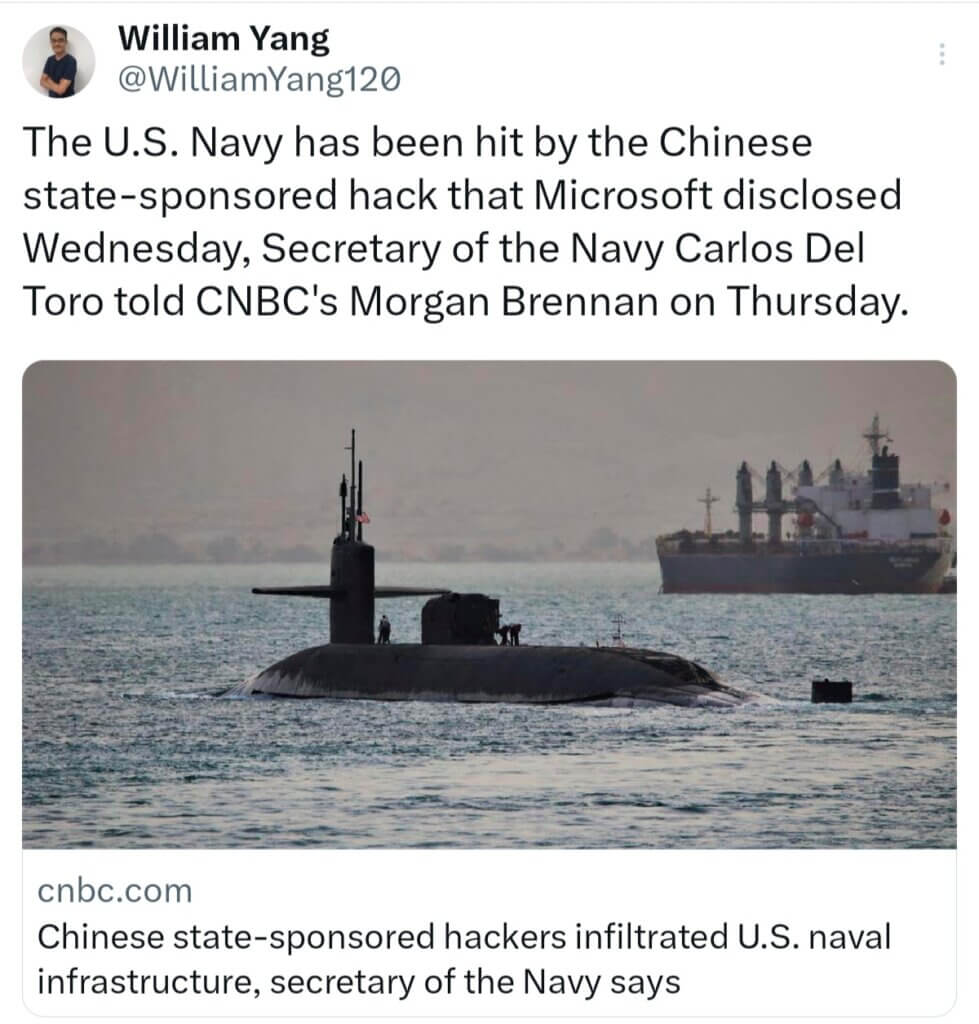
The threat of Chinese cyberattacks on global infrastructure is a significant concern. Chinese state-sponsored hacking has emerged as a critical global threat, targeting vital infrastructure across multiple nations. Recent reports reveal that Chinese military hackers have infiltrated Japan’s defense networks since 2020, accessing classified information about military capabilities and strategic plans. This breach, discovered by the U.S. National Security Agency, highlights the deep and persistent nature of Chinese cyber espionage. Despite efforts to secure these systems, the continued breaches underscore the sophistication and persistence of Chinese cyber capabilities. Additionally, China-based hackers have targeted U.S. government agencies, including the State and Commerce Departments, and critical sectors like transportation and utilities. These attacks are part of a broader strategy to gain access to sensitive information and disrupt vital infrastructure.
Additionally, recent reports indicate a troubling rise in cyberattacks against our critical infrastructure, including water supplies, by actors linked to China, Russia, and Iran. These cyberattacks do not just target water utilities but extend to other critical infrastructure, telecommunications networks, and security systems. They can disrupt access to essential services, steal intellectual property, and undermine our trade networks. The increasing frequency and sophistication of these attacks pose a significant threat to our national security and economic stability.
While Mead raises valid points about the severity of the threats we face, his politicization of the issue is counterproductive. The truth is, there is ample blame to go around, and what we need now more than ever is education and transparency. Americans deserve to understand the stakes and be assured of the integrity of those advocating for stronger defense measures. This is not a right versus left issue—it’s an American issue that requires a united, all-hands-on-deck approach.
A key mission of Americans for a Stronger Navy is to educate the public about these security challenges and the need for a stronger Navy. By fostering a national dialogue, we can bridge the gap between policymakers and the public, fostering mutual understanding and engagement. It is also crucial to emphasize the need for bipartisan cooperation in addressing these threats. A unified approach is necessary to effectively respond to the complex and evolving global security landscape.
In sum, the threats are indeed formidable, but trust is in short supply. Addressing this requires a commitment to honesty and clarity from our leaders, ensuring that the American public is both informed and engaged in the security decisions that will shape our future.
Thanks for listening.
Bill,
Americans for a Stronger Navy